灯塔实验室技术沙龙(第四期)主题为“工控系统威胁分析技术”,讨论话题将涉及工控系统威胁感知监测技术、工控系统威胁捕获方式、威胁数据的分析处理方法等相关话题。
灯塔安全沙龙秉承开放讨论,自由分享的理念,鼓励出席参与者都能分享技术见解和心得,不限分享风格与形式。
本次沙龙活动于2017年3月18日在北京市海淀区中关村大街新七天咖啡厅圆满举行完毕,以下是来宾在沙龙上的议题汇总。
《常见工控漏洞分析和态势感知》分享人:Z-0ne
来自灯塔实验室的Z-0ne在本次沙龙上分享了关于工控系统里常见的组件及组件存在的漏洞和缺陷。Z-0ne在分享中详细介绍了从PLC/RTU到SCADA组态软件以及工控通信设备存在的漏洞,并分享了每类组件连接到互联网的数量和利用组件漏洞进行渗透的案例。最后,Z-0ne还介绍了灯塔的工控系统态势感知计划,展现了灯塔实验室态势感知的能力。
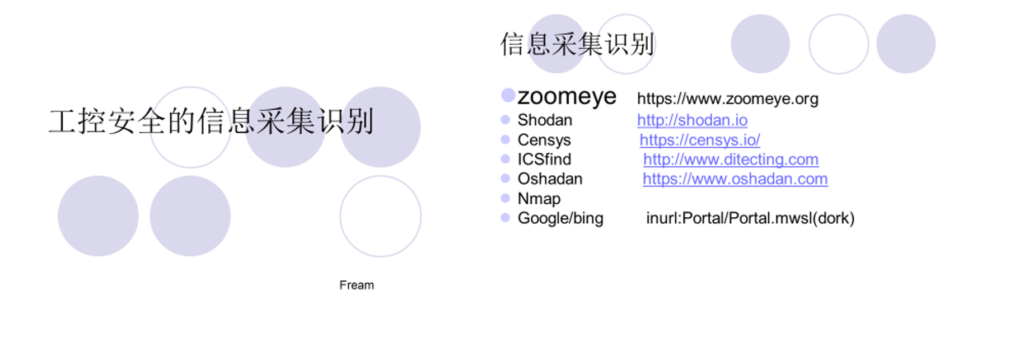
《工控安全的信息采集识别》分享人:Fream(丁毅)
来自知道创宇的Fream为大家分享了关于工控安全常见信息采集识别的一些手段,详细介绍了ZoomEye的工控协议的数据检索情况,展示了ZoomEye的常见端口和对应的协议。
《如何通过分析平台追踪可疑来源》 分享人:赵林林
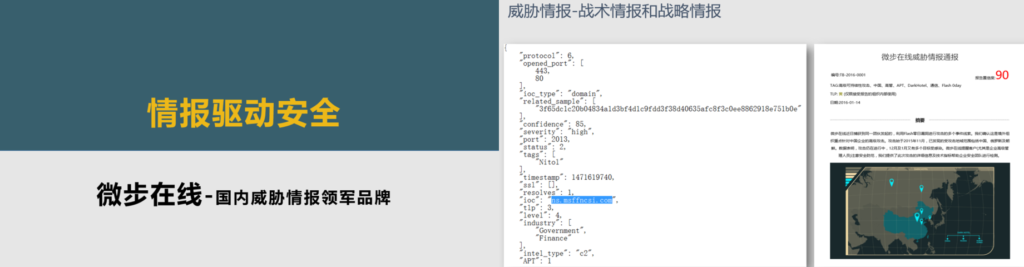
《微步在线:情报驱动安全》 分享人:王诗梦
来自微步在线的赵林林通过为大家介绍几个生动精彩的威胁溯源案例,表示溯源是一个缓慢的过程,前期需要收集大量的资料,对动态域名进行持续的积累。为了让大家进一步了解了微步在线在威胁情报方面的工作,王诗梦为大家分享了微步在线关于威胁情报的理念,即只有对攻击者的动机、资源、工具、战术方法及行为过程等诸多方面有足够的了解,即掌握足够多的数据,才能有效的检测和响应,而高效的检测和响应技术是新时代下建立有效防御体系的核心。最后,她为参会来宾介绍了微步在线基于基础情报能力,以及情报数据订阅服务、威胁分析云服务、溯源追踪系统、威胁情报平台。
《Fireeye工控安全报告》 分享人:谢瑞璇
来自启明星辰从事多年漏洞扫描、威胁情报等安全研究工作的谢瑞璇,将近几年的Fireeye、卡巴斯基和CNVD披露的工控漏洞进行了汇总展示,并指出了国内外不同机构对工控漏洞统计数据各不相同,这其中应该不只是技术手段或视角的不同,同时,通过对2016年重大工控安全事件的回顾,与大家一起对工控安全发展的未来进行讨论和展望。
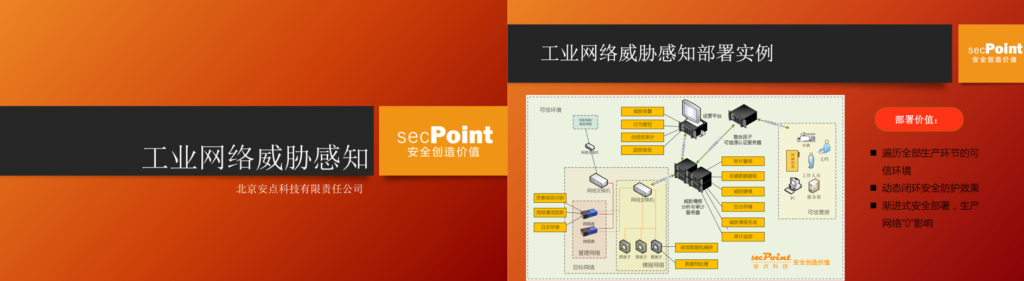
《工业网络威胁感知》 分享人:罗艳
来自安点科技先进实验室的负责人罗艳首先为我们介绍了国内工业企业目前普遍安全现状,针对工业系统网络常见的脆弱性特点建立的工业闭环防御模型。安点科技还提出了企业环境下的网络威胁感知系统及其被动式扫描引擎、资产发现、行为建模、可视化展示的功能,并对其工控协议的深度解析进行了阐述。
《谛听工业网络空间安全态势感知平台》 分享人:盛川
来自东北大学姚羽教授发起并组织的谛听网络安全团队代表盛川,通过“谛听”的演变进程、主要内容、改进方向三个方面介绍了 “谛听”工业网络空间安全态势感知平台,同时重点为我们大家分享了谛听的数据采集系统和数据分析系统,以及如何用数据分析系统支持国家的基础设施大检查的落地。
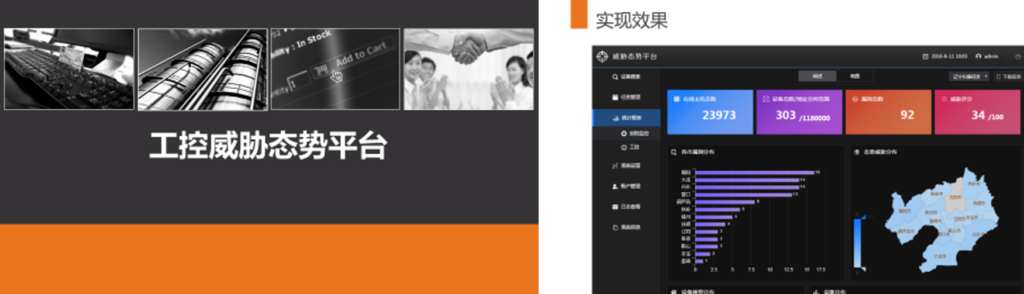
《工控威胁态势平台》 分享人:姜双林
来自华创工匠实验室负责人,前匡恩网络高级安全研究员姜双林为大家分享了工控安全威胁态势平台产品化面临的问题,即产品化向着小型化、弹性扩展发展的路线以及部署场景,并为大家重点介绍了威胁态势平台基于优先级的分布式流水线扫描引擎和实现的效果。
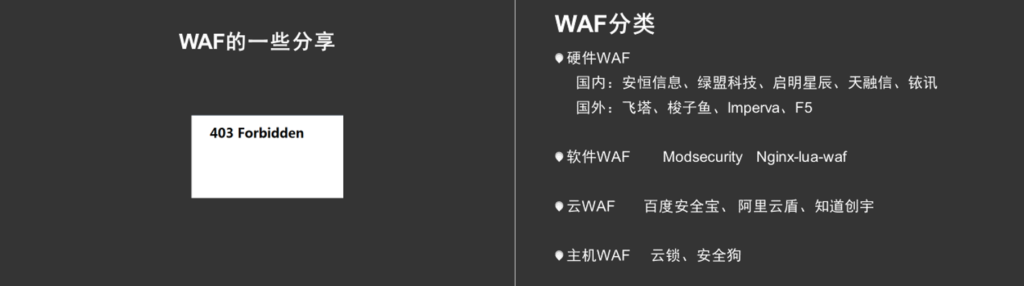
《WAF的一些分享》穆立博
来自天融信的穆立博为大家介绍了WAF的发展,WAF的分类,WAF的防御手段以及WAF绕过技术,并且提出工控设备如果可以被互联网访问的话,建议增加WAF针对Web SCADA的针对性防御功能。
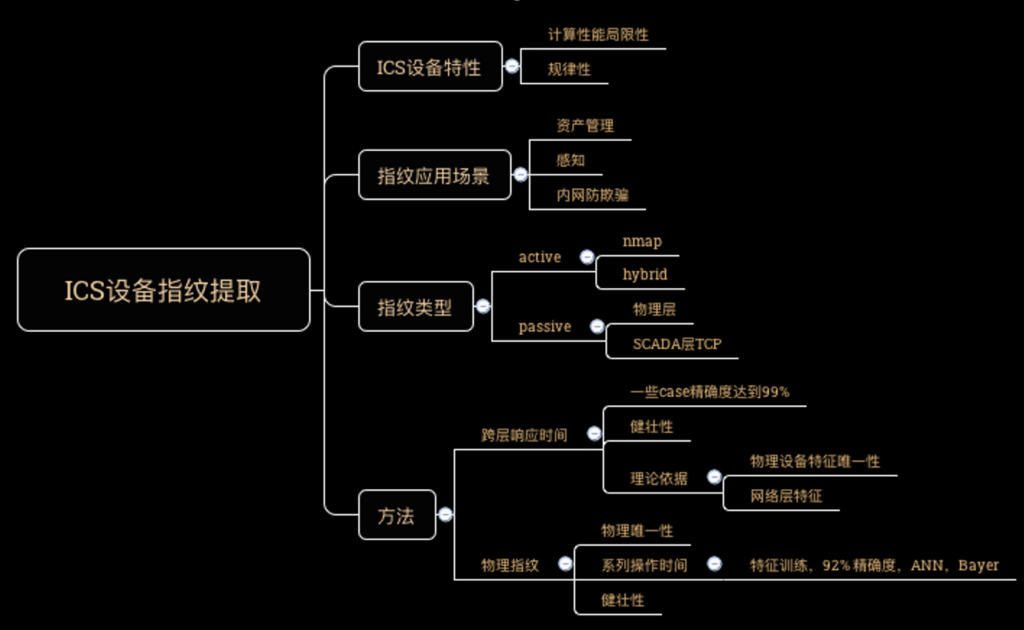
《ICS设备指纹提取》程鹏
工控安全技术的个人爱好者程鹏为大家分享了国内和国外关于工控设备指纹提取方面的论文的核心观点和实验情况,包括工控设备的特性,工控设备指纹应用的场景,指纹类型以及指纹提取的方法,关于其中提到的被动检测技术程鹏将进一步形成详细材料通过灯塔平台发布。
《美国网络风暴行动后工控系统威胁感知》Kimon
来自灯塔实验室的Kimon为大家分享了美国近几年针对网络空间的演习行动,从规模、模式、效果进行了分析归纳,并结合灯塔实验室针对控制系统威胁感知技术,重点为参会来宾展示了灯塔实验室对全网的工控系统威胁感知方式,以及灯塔安全中心是如何感知网络实战行动前后的态势及变化趋势。

最后Kimon又为来嘉宾们介绍了灯塔实验室“合伙人发展模式”,讲解了灯塔研究员、灯塔专家及灯塔合伙人三个不同角色的责任和义务,并宣布灯塔实验室正式对外招募三类角色。
此外,Skylab实验室的杨海清与大家分享了他们在工控安全测评项目中遇到的问题,来自全球能源互联网研究院的费稼轩也和大家讨论了在电网配电端是否还存在安全问题,来自中科院信息工程研究所的孙利民教授作为本次活动的特邀嘉宾认真听取了报告并参与了技术讨论。